PREFACE
To help companies and organizations which have security requirements understand the basic state of China cybersecurity companies, Aqniu lanuched “China Cybersecurity Companies Top 50″(CCCT) investigation efforts in mid-July. This survey targeted on cybersecurity companies itself. And this kind of efforts is the first time in China. Also the number of respondents is unprecedented in China.
The investigation selected 100 candidates from more than 400 security companies. The ways of survey include completing the survey form, telephone interview, meeting, and collecting public data. The committee consists of senior security engineers , experienced experts on security industry, and media professionals, according to the designed indicators and survey methodology, combined with the creation time of the companies, product types and operation mechanism, named 50 companies as Top 50 in the 100 candidates. The whole survey process took more than thress months, and listed four types of company, the traditionals, the emergings, the start-ups and the network security department of large enterprises.
The full report issued by cybersecutiry new media platforms–Aqniu on October 27, 2015 , as well as released in english for the global, to provide a reference for related industries and institutions around the world to understand the basic state of cybersecurity comanies of China.
China Cybersecurity Companies Top 50
1. The Traditionals Top 25
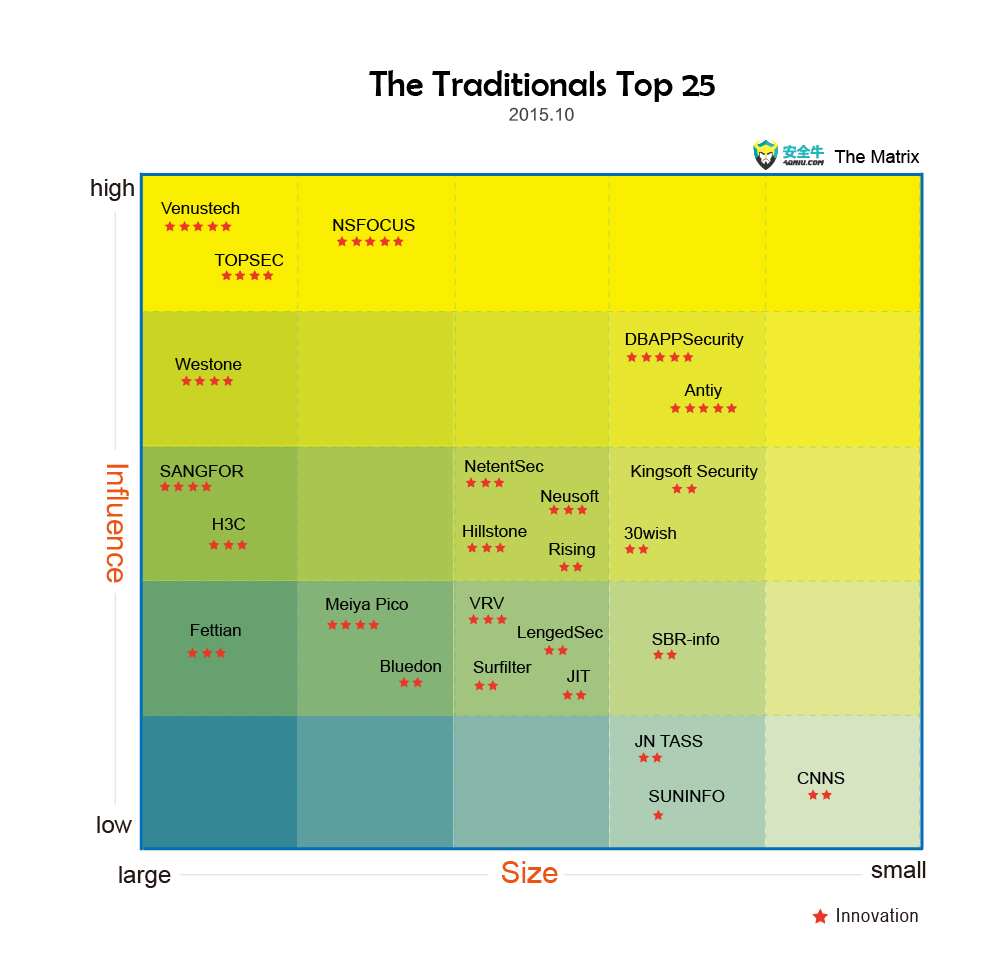 (Note: the size of company mainly refers to the number of personnel and income level, the influence mainly mainly refers to the industry users’ visibility, recognition and media exposure)
(Note: the size of company mainly refers to the number of personnel and income level, the influence mainly mainly refers to the industry users’ visibility, recognition and media exposure)
Products & Services :
(By Numerical and Alphabetical Order)
30WISH: information security, consulting, systems integration, system operation and maintenance and software applications of the five services, industrial firewalls.
ANTIY:network and mobile network virus monitoring system, host security inspection system and the emergency response supporting , risk assessment and other services.
BLUEDON: security gateways and audit, classified / terminal / application security products, firewalls and intrusion prevention, information security consulting, training and risk assessment.
CNNS:security service provider, provide vulnerability management, penetration testing platform.
DBAPPSECURITY:web application security, WAF, database audit, security gateways, and Information security level of protection inspectio, site safety monitoring, APT attack protection, big data security center of the storm, providing emergency response supporting, security training, risk assessment, penetration testing and other security services.
FEITIAN: smart card operating systems and digital security system as a whole solution, including network authentication, software copyright protection in the field of smart card operating systems and.
H3C: security gateway, intrusion prevention, security management center, Web security, security audits, vulnerability scanning, providing security research, solutions and services, virus signatures.
HILLSTONE: next-generation firewall, Web application firewall, intrusion prevention, security management, security audit, virtualization, cloud security.
JIT: PKI product and service providers, including electronic certificates, authentication, rights management, directory services, secure transmission, electronic signature, passwords and other credentials.
JN TASS: commercial encryption products, security management products, the offensive and defensive test products, and provides security assessments, consulting, implementation, operation and maintenance and other services.
KINGSOFT SECURITY: Terminal Antivirus / virtualization / private cloud / Mobile Security / APT protection system, integrated platform, antivirus gateways, security systems customized for localization.
LENGEDSEC: security gateway, intrusion prevention, network gateway, server security hardening, vulnerability scanning, virus killing, providing network and information security systems design, planning and solutions, risk assessment, safety operation and maintenance of security, emergency response.
MEIYA PICO: electronic data forensics products and network information security products, the two product lines, as well as electronic data authentication services and Internet services to the two digital intellectual property protection service system.
NETENTSEC: Three product families: network security, network management and network traffic optimization; seven product lines including Internet control gateway and next-generation firewall; new-generation “NGFW + Wise Eye” host breach detection solution.
NEUSOFT: security gateway, intrusion prevention, security management, traffic management, security audit, security risk assessment, professional security services and network security solutions.
NSFOCUS: Anti-DDoS, firewall, intrusion prevention, Web security, threat analysis, data leakage, vulnerability scanning, providing site security testing, consulting and training services.
RISING: Endpoint security, virtualization security, gateway anti-virus wall, network warning, Internet behavior management, mobility management, network version and Personal Edition antivirus software and other core technology of the overall solution.
SANGFOR: to provide users with next-generation firewall, security products and risk assessment SSL VPN, Internet behavior management, security scanning, penetration testing, security reinforcement, and other insurance consulting, emergency response and other full-service security system.
SBR-INFO: bastion host, internal network security management system, removable storage media management system, integrated management information system security protection, network audit system.
SUNINFO:information security consulting and evaluation of data security products, compliance and audit products, end integrated security products, gateway security products, information security solutions integration service providers.
SURFILTER: NET110 security audit, network security management, IDC security audit, Internet public opinion analysis and management systems, next-generation firewalls, next-generation unified threat management, WEB application firewall.
TOPSEC:Web security, data / database security, security / anti-virus gateway, intrusion prevention, anti-DDoS, application delivery, Internet behavior management, endpoint security management and compliance audits, security management, operation and maintenance monitoring, consultation and evaluation, security training services.
VENUSTECH:security gateway, intrusion prevention, anti-DDoS, vulnerability scanning, security audit, security management platform, data security, terminal management and anti-virus, industrial safety, information security consulting and risk assessment services.
VRV:endpoint security, data security products and integrated solutions vendor, covering traditional windows terminal, a mobile terminal, independent domestic terminal, virtual terminal and so the whole type of endpoint security management.
WESTONE:Password equipment, cryptographic modules, cryptography, network security, host security, data security and security management, secure desktop cloud, secure storage, electronic documents, security office, security infrastructure platform, independent Trusted Computer.
2.The Emergings Top 10
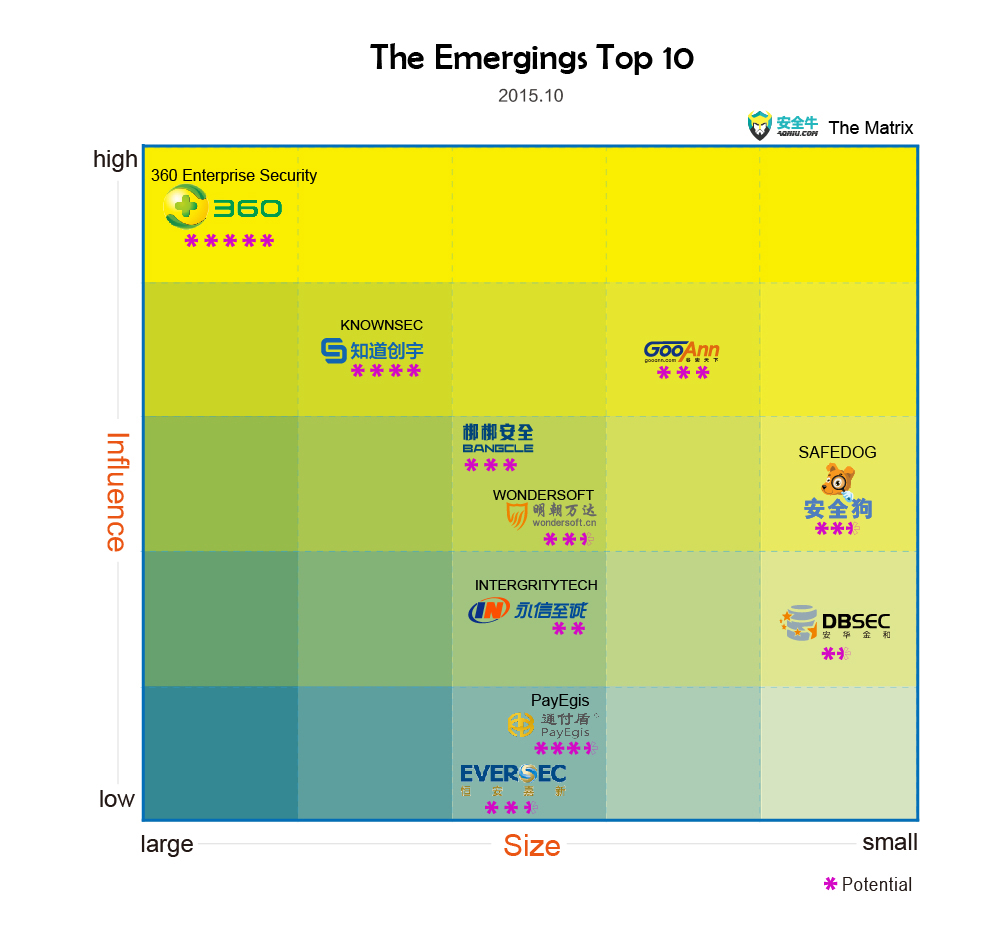 (Note: the size of company mainly refers to the number of personnel and income level, the influence mainly mainly refers to the industry users’ visibility, recognition and media exposure)
(Note: the size of company mainly refers to the number of personnel and income level, the influence mainly mainly refers to the industry users’ visibility, recognition and media exposure)
Products and Services :
(By numerical and Alphabetical Order)
360 ENTERPRISE SECURITY: Terminal integrated security management system, including antivirus, terminal management, virtualization, cloud security, access controlling, host security and so on. Mobile terminal security management system and wireless intrusion prevention systems.
BANGCLE: Mobile application security assessments, penetration testing, mobile application reinforcement, channel monitoring, data services.
DBSEC:Database security products and services, including database leaks scan, database safe and database firewall, database audit.
EVERSEC: Telecommunications network security products, IT security configure automatic audit platform and document security solutions, network security services.
GOOANN:Information security consulting and services, IT Governance and IT audit services, security professional training and education, online education, IT-GRC software, new media services.
INTERFRITYTECH:Network security confrontation training platform, network sensitive data detection system, password security test systems, Internet security access systems, on-line education.
KNOWNSEC:Internet cloud security monitoring, site security assessments, cloud WAF, cloud acceleration, site URL security, security search engines.
PAYEGIS: Internet banking security services, including application security cloud service, authentication cloud services, Big Data analytics cloud services.
SAFEDOG: Server security, website security, cloud security, cloud backup.
WONDERSOFT:Data security products and services, including data protection, file encryption, application protection, systems management, desktop management and security communications, data security management and mobile security management platform.
3.The Network Security Department of Large Enterprises
Brief Introduction:
(By Alphabetical Order)
ALI SECURITY
Main security business sectors: business security, operational security, data security, infrastructure security, mobile security, cloud security, data and algorithms, standards and new technologies, Surporting Taobao, Tmall, Ali cloud, B2B, Air Travel, Wireless, Digital Entertainment, and all Ali Group’s b rands and business.
Total security team personnel 2000+.
The advantages of Ali Security, based on a comprehensive account security, information protection, fraud management mechanism, using big data to build powerful real-time risk control and network defense capability.
The mission of Ali security is to “Protect The Wallet”, “Protect Career”, “Promoting Integrity” and “Help Development”, solving the most security problems users are concerned with, building the world’s leading risk control and network Attack & defense capabilities which based on the big data technology.
BAIDU SECURITY
Baidu security business is comprised of four groups, Cloud Security which is also responsible for corporate security, Mobile Security, PC Security, and Security Research Labs. Baidu has several lines of security products, which include cloud security products, such as YunJiaSu, AnQuanBao and DDoS Migitaion services, mobile and PC security client products.
Baidu security teams have more than 1000 employees. Baidu security products hundreds of millions of consumer users, hundreds of thousands of web sites and applications, thousands of top tier enterprises, and the majority of domestic cloud computing platforms.
Taking root in its world class search technology and state-of-art deep learning technologies, Baidu security provides unique and highly effective products and services to help build a safe and secure internet.
Baidu’s strategy on security is focus on building a trusted and secure internet ecosystem, upon which to build its product and service value, centering around Baidu’s overarching goals. Monetary return is therefore not a high priority for Baidu security in a short term.
CHINA TELECOM SECURITY
Full security services are summarized in three aspects: China Telecom Tianyi cloud computing security sub-series products, including WAF, virus and worm detection, as well as security perception analysis; backbone carriers’ “pipe” services such as “cloud dike” DDoS attack protection services; terminals, including mobile terminal hardware and software.
In addition, China Telecom systems integration company and provincial branches have some other personalized security service products, such as Website
Security Housekeeper , security risk assessment reviews and other services.
Total security team personnel 1000+,providing security services for a few hundred millions of broadbandusers and ten millions of mobile users. Enterprise users is thousands of , secure income up to a few hundred millions yuan.
China Telecom’s security strategy, achieve carriers differentiationcompetitive advantage and enhance the value of added services and traditional resource-based business customers viscosity. On the market, China Telecom’s advantages are the network technology team that has rich experiences, a strong network capability, a large number of government and enterprise customer resources and continue to exploit the potential of the consumer market.
HUAWEI SECURITY
Huawei security covering a number of areas including endpoint security, network security, cloud security, application security, security management and security services, also has a separate internal security competence center. Security products include high-low end next-generation firewall, intrusion prevention, DDoS defense systems, virtual integrated services gateway, APT defense system, analysis of large data security systems and other products, and the related solutions to traditional threats and unknown threats.
Total security team personnel 2000+. Huawei’s teles or carriers costumers which cover most global TOP 50. Its business users reach up to a few of hundred thousands, the annual sales income of global security products is over 1 billion yuan.
The advantages of Huawei Security are based on its brands and sale channels around the world, as well as its continued high annual investment in reseach and development to ensure the competitiveness of products and future visions.
On security strategy, Huawei is building a fully connected secure network, and is committed to creating a more open ecosystem, to provide users with end-to-end products and solutions.
TENCENT SECURITY
Total security team personnel 1000+, distributed among each departments and Business Groups
Security Product Line: Client-side security , cloud security, internal security.
Security services: C-side Security mainly consists of Tencent Computer Butler and Mobile Butler;Cloud Security is mainly to provide anti-DDoS services, vulnerability scanning, and work with other security vendors;Internal Security service mainly for Tencent own, including operational security, business security, gaming security and so on.
The number of users: C-side security is about a few hundred millions , Cloud security is a few hundred thousands.
Security Advantages: Tencent has ten years of experience which accumulated from fighting with the dark industry , through analysis of large data systems, Tencent has the ability to provide quality security services for the Client-side and business-side users.
Security Strategy: With the abilities accumulated over the years, Tencent’s future will be open to users its security products, to enhance the overall Internet security capabilities. At the same time, together with industry partners, to create cloud security ecosystem.
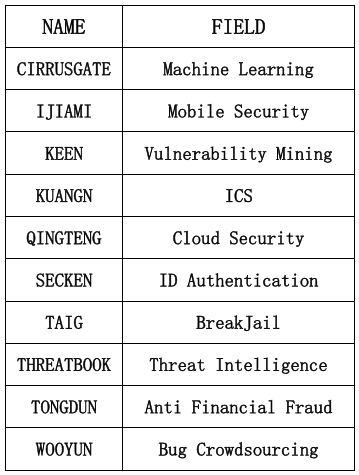
4.The Start-ups Top 10
Over the recent years, dozens of cybersecurity start-ups is surging in China. Aqniu recommended 10 start-ups as the most representative companies in 10 security fields.
(By Alphabetical Order)
5.Additional Information
The survey obtained the support and help of vast majority cybersecurity companies. However there are a few of enterprises gived up participating in this invtestigation voluntarily for some reasons, so the results of this survey do not represent the status of the whole cybersecurity companies of China. But even those who did not participate in the survey, all of them expressed interests in this report and expressed willingness to participate in the next survey. Aqniu will update “CCCT 50” regularly with more professional, strict and thorough efforts. Welcome everyone to give CCCT attentions and supports.
Thanks!
Annex Ⅰ
26 Survey indicators:
Sales revenue, annual profit, staff size, market capitalization or valuation, growth rate, the amount of financing, number of customers, customer growth, covering industry, covering the sector, the number of new product releases, the number of patents, talent introduction, average pay, per capita output, operating costs, user coverage, media coverage, background, people attractiveness, staff turnover, employee satisfaction, quality and technology, product or service, customer satisfaction.
Annex Ⅱ
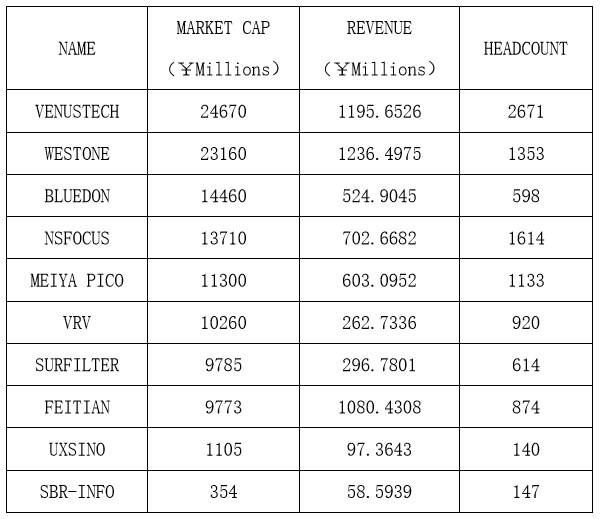
(By Market Cap Order)